In the ever-evolving realm of cryptocurrency, securing digital assets is paramount. Among the various security measures available, hardware wallets have emerged as the Fort Knox of digital currency storage. These devices, often no larger than a USB stick, serve as a physical vault for cryptocurrencies, offering unparalleled security in an increasingly digital world.
What is a Hardware Wallet?
A hardware wallet is a physical device that stores the private keys necessary to access and manage cryptocurrencies offline. This form of ‘cold storage’ is detached from the internet, making it virtually immune to online hacking attempts, a prevalent threat in the digital currency space. Unlike ‘hot wallets’ (software wallets connected to the internet), hardware wallets provide a robust layer of security by keeping the user’s private keys completely offline when not in use.
Why Hardware Wallets are Crucial in the Cryptocurrency Ecosystem
Increased Security: The primary advantage of a hardware wallet is its ability to provide enhanced security. By storing private keys offline, these devices are immune to online vulnerabilities like phishing attacks, malware, and unauthorized remote access.
Ownership and Control: Hardware wallets put the control of assets directly in the hands of the user. Unlike online exchanges or wallets, where the private keys are often held by a third party, hardware wallets ensure that the user maintains full control over their digital assets.
Portability and Ease of Use: Despite their advanced security features, hardware wallets are designed for convenience. They are portable, easy to use, and compatible with various cryptocurrencies, making them a versatile choice for both beginners and seasoned crypto enthusiasts.
Recovery Features: In case of loss or damage, hardware wallets provide secure recovery options. Users can restore their funds using a unique recovery phrase provided during the initial setup of the device.
The Growth of Hardware Wallets
The demand for hardware wallets has surged with the rise of cryptocurrency. As digital currencies like Bitcoin, Ethereum, and others gain mainstream acceptance, the need for secure storage solutions becomes more critical. This demand has led to a variety of models and features offered by different manufacturers, catering to a range of preferences and security needs.
How Hardware Wallets Work

Understanding the mechanics of hardware wallets is key to appreciating their role in cryptocurrency security. At their core, these devices are dedicated to safeguarding private keys, the critical piece of data required to authorize cryptocurrency transactions.
Technical Operation of Hardware Wallets
Hardware wallets function by creating and storing private keys within a secure chip on the device. This process is conducted offline, ensuring that the keys are never exposed to an internet-connected environment. When a transaction is initiated, the user connects the hardware wallet to a computer or mobile device. The transaction is then digitally signed inside the wallet, without the private keys ever leaving the device. This method of transaction signing is what sets hardware wallets apart in terms of security.
Cold Storage: The Ultimate Safeguard
The concept of ‘cold storage’ is central to hardware wallets. By keeping private keys offline at all times except when transactions are being signed, these wallets ensure that the keys are not susceptible to online attacks, such as hacking or phishing. This offline storage method is akin to keeping valuable assets in a physical safe rather than in a potentially vulnerable online account.
Security Protocols and Features
Hardware wallets are equipped with several layers of security to ensure the safety of digital assets. These include:
- PIN Codes: To access the device, users must enter a PIN code, adding an additional layer of security against physical theft or unauthorized access.
- End-to-End Encryption: Communication between the hardware wallet and the connected computer or phone is fully encrypted, preventing interception or tampering.
- Secure Element Chips: Many hardware wallets use secure element chips, the same technology used in credit cards and passports, to protect against physical and digital tampering.
User Interaction with Hardware Wallets
Despite the sophisticated technology behind them, hardware wallets are designed for ease of use. They typically feature a small screen to display transaction details and buttons to navigate and confirm actions. This simple interface allows users to securely manage their assets without needing technical expertise.
The Security Architecture of Hardware Wallets
The high level of security offered by hardware wallets is not just a matter of convenience but a critical necessity in the realm of cryptocurrency. This section delves into the specific features and design elements that make hardware wallets a bulwark against various threats.
Multi-Layered Security Approach
Hardware wallets employ a multi-layered approach to security, combining hardware and software measures to create a comprehensive defense system. This approach includes:
Physical Durability: Many hardware wallets are built with resilience in mind, featuring robust casings and resistance to physical damage.
Isolation of Private Keys: The private keys never leave the device, ensuring they are not exposed to online vulnerabilities.
Tamper-Proof Design: The physical design of these wallets often includes features to detect and prevent tampering, ensuring the integrity of the device.
Immunity to Online Threats
One of the most significant advantages of hardware wallets is their immunity to online threats, a common concern in the digital asset world. Since the private keys are stored offline, they are safe from:
- Phishing Attacks: Scams that trick users into revealing sensitive information.
- Malware and Viruses: Malicious software that could compromise online wallets.
- Remote Hacking Attempts: Unauthorized access attempts from remote locations.
User Verification Processes
To further enhance security, hardware wallets incorporate several user verification processes, such as:
- PIN Codes and Passphrases: These are required to access the device, adding an extra layer of security.
- Transaction Verification: The wallets display transaction details on their screens, allowing users to verify and manually confirm each transaction.
- Recovery Phrases: In case of device loss or damage, users can recover their funds using a unique recovery phrase provided during the initial setup.
Compliance with Security Standards
Many hardware wallets comply with rigorous security standards, undergoing extensive testing and certification to ensure they meet industry benchmarks. This compliance provides an additional assurance of their reliability and safety.
The security architecture of hardware wallets is designed to protect against both physical and digital threats, offering a level of safety that is essential for managing valuable digital assets. This robust security framework not only safeguards the assets but also instills confidence in users, knowing their investments are secure.
Comparative Analysis of Popular Hardware Wallet Models
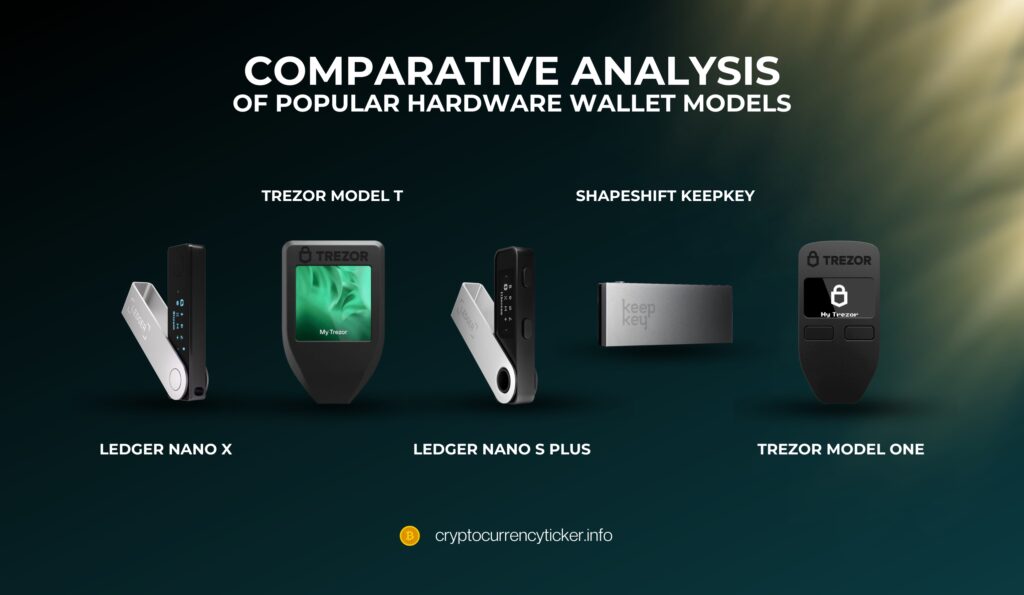
When it comes to selecting a hardware wallet, the choices can be overwhelming. Each model has its unique features, benefits, and limitations. Here, we compare some of the most popular hardware wallets to help users make an informed decision tailored to their specific needs.
Ledger Nano X
Features: Equipped with Bluetooth connectivity, supports over 1,800 cryptocurrencies, and includes a built-in battery for mobile use.
Pros: Offers a high capacity for multiple cryptocurrencies, a user-friendly interface, and is portable with wireless connectivity for on-the-go use.
Cons: Comes at a higher price point, and some users may have security concerns regarding Bluetooth connectivity.
Trezor Model T
- Features: Features a color touchscreen, supports hundreds of cryptocurrencies, and operates with open-source software.
- Pros: Enhanced security with a full touchscreen interface, easy backup and recovery process, and strong community and developer support.
- Cons: Priced higher than some alternatives, lacks Bluetooth or wireless connectivity.
Ledger Nano S Plus
Features: Similar to the Ledger Nano X but without Bluetooth, it supports a wide array of cryptocurrencies.
Pros: More budget-friendly than the Nano X, compact and durable design, maintains high-level security features.
Cons: Lacks wireless connectivity and has a smaller screen size compared to its advanced counterpart.
ShapeShift KeepKey
- Features: Boasts a large display, supports multiple cryptocurrencies, and is integrated with ShapeShift for direct crypto exchanges.
- Pros: Affordable, straightforward backup and recovery process, and a larger screen for easier use.
- Cons: Bulkier design compared to others and a potentially slower interface.
Trezor Model One
Features: Compact design, supports many popular cryptocurrencies, and features an easy-to-use interface.
Pros: More accessible price point, reliable security features, and straightforward setup and usage.
Cons: No touchscreen facility, limited coin support in comparison to the Model T.
User Experience: Setting Up and Using a Hardware Wallet
The practicality of hardware wallets extends beyond their security features. For many users, the ease of setting up and using these devices is a crucial factor. This part of the article focuses on the general steps involved in setting up a hardware wallet and the user experience in managing cryptocurrencies with these devices.
Initial Setup
- Unboxing and Device Initialization: The first step involves unboxing the hardware wallet and powering it on. Most wallets will guide users through an initialization process.
- Creating a PIN Code: Users are prompted to create a PIN code, a crucial security measure to access the wallet.
- Generating the Recovery Phrase: During setup, the wallet generates a recovery phrase, typically 12 to 24 words long. This phrase is critical for restoring access to the wallet’s contents in case the device is lost or damaged.
- Installing Companion Software: Most hardware wallets require the installation of companion software on a computer or smartphone. This software interfaces with the wallet for transaction management.
Daily Usage
Connecting to a Computer or Smartphone: To perform transactions, users connect their hardware wallet to a device with internet access.
Transaction Management: The companion software or app allows users to manage their cryptocurrency portfolio, including sending and receiving digital assets.
Verifying Transactions on the Wallet: For added security, each transaction must be verified and confirmed on the wallet’s physical interface.
Safely Disconnecting After Use: Once transactions are completed, it’s crucial to disconnect the hardware wallet and store it securely.
User-Friendly Features

Hardware wallets offer several advantages that cater to the needs of cryptocurrency users. They often feature intuitive interfaces with screens and buttons, facilitating easy navigation and allowing users to verify and confirm transactions with confidence. Another key benefit is their multi-currency support, enabling users to manage a wide array of cryptocurrencies within a single device, making these wallets versatile tools for both investors and enthusiasts.
Additionally, hardware wallet manufacturers prioritize security by regularly releasing firmware updates. These updates not only enhance security measures but also add new features, ensuring that the device remains current with the latest developments in the dynamic cryptocurrency landscape. This comprehensive approach to usability, versatility, and security makes hardware wallets a favored choice among those looking to protect and manage their digital assets effectively.
Future of Hardware Wallets: Innovations and Trends
The landscape of cryptocurrency is dynamic, with continuous advancements and evolving security challenges. As such, the future of hardware wallets is poised to be shaped by ongoing innovations and emerging trends. This forward-looking perspective explores potential developments in hardware wallet technology and how they might influence the way users interact with and secure their digital assets.
Emerging Technologies in Hardware Wallets
Biometric Security: Future models of hardware wallets may incorporate biometric features, like fingerprint recognition, to add another layer of security.
Wireless Connectivity Enhancements: Improvements in secure wireless technologies could make hardware wallets more convenient while maintaining high security standards.
Integration with Decentralized Applications (DApps): Enhanced compatibility with DApps is likely, allowing users to interact directly with decentralized finance (DeFi) platforms and other blockchain-based applications.
Predictions for Future Developments
In the future, hardware wallets are expected to feature advanced multi-signature capabilities, providing extra security. They’ll also need increased storage capacity to accommodate the expanding variety of cryptocurrencies. Additionally, there’s a growing focus on environmentally friendly designs, with an emphasis on sustainable materials and manufacturing processes.
Trends Influencing Hardware Wallet Adoption
- Mainstream Cryptocurrency Adoption: As cryptocurrencies become more integrated into everyday finance, the demand for secure and easy-to-use hardware wallets is likely to grow.
- Enhanced User Experience: Continued emphasis on user-friendly design and interfaces will make hardware wallets more accessible to a broader audience.
- Regulatory Changes: Changes in cryptocurrency regulations may influence the features and security protocols of hardware wallets, as compliance becomes increasingly important.
Conclusion
Hardware wallets are essential for securing cryptocurrencies, combining strong security with user-friendly interfaces. Their evolution underscores their importance in the growing digital currency world, signifying a matured ecosystem where security and convenience coexist.
Looking forward, their significance will increase with the expanding digital currency realm. As the crypto market evolves, the need for reliable and secure storage solutions becomes paramount. Hardware wallets, with their continuous innovations, are poised to meet these challenges, acting as the Fort Knox of cryptocurrency, protecting digital assets now and in the future.
